Unmanaged Permissions are Expanding Your Attack Surface
The adoption of multicloud has brought great benefits to organizations – but inadvertently created a new attack surface that did not exist 5 years ago. In fact, over 40K permissions exist across the key cloud platforms, and nearly 50% are estimated to be high-risk and could cause catastrophic damage if used improperly, such as, service disruption, service degradation or data exfiltration. To make matters worse, we’ve discovered that more than
90% of identities (both human and workload) use less than 5% of the permissions they are granted to perform their daily tasks
– leaving the other 95% of unused permissions wide-open to accidental misuse or intentional exploitation of permissions.
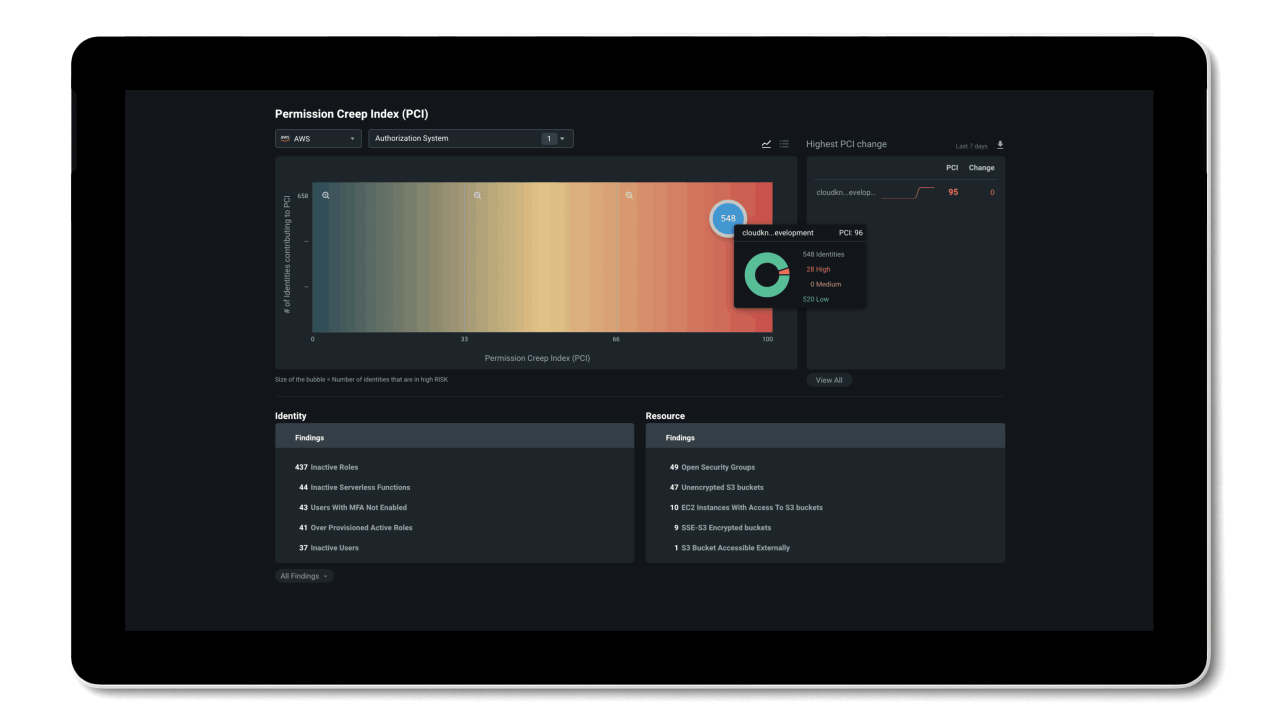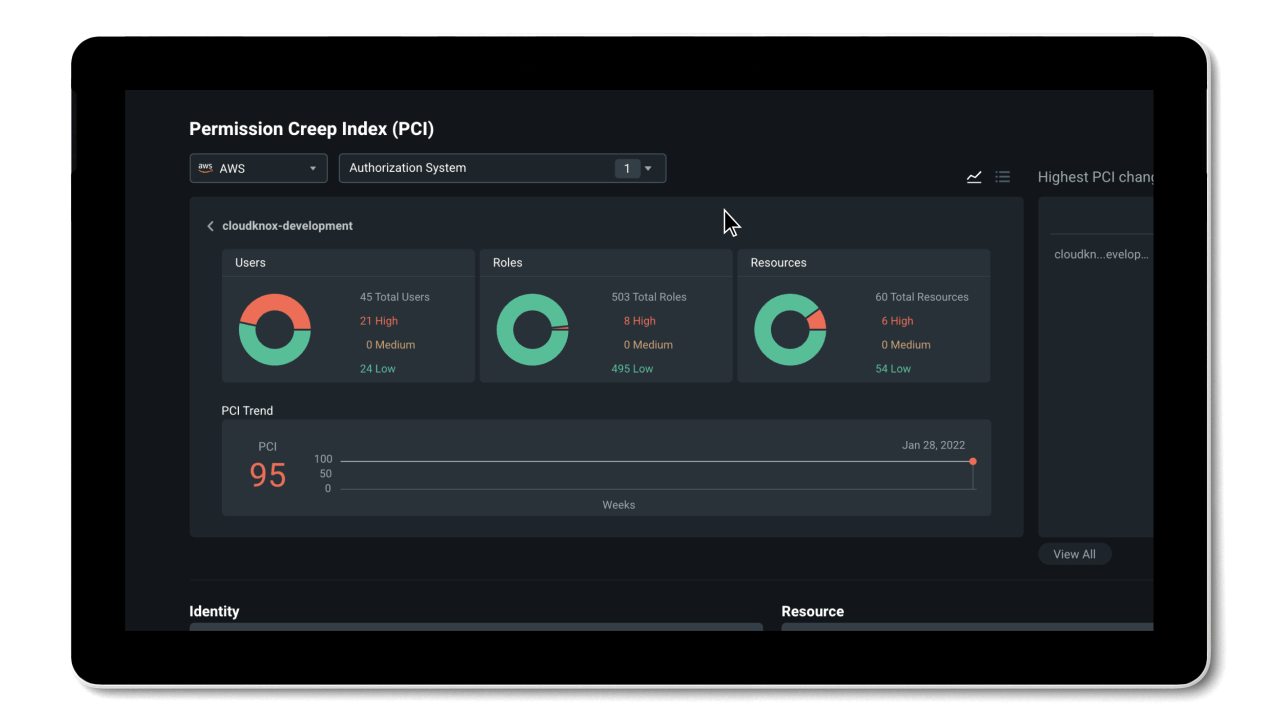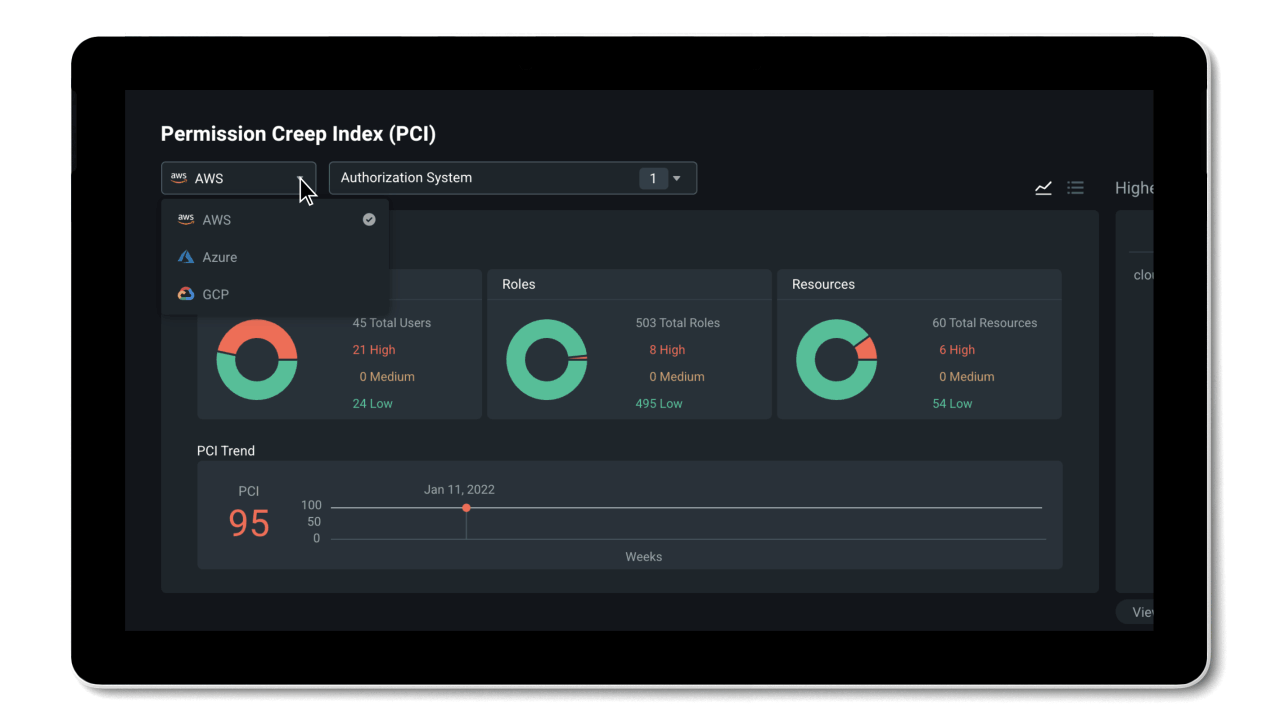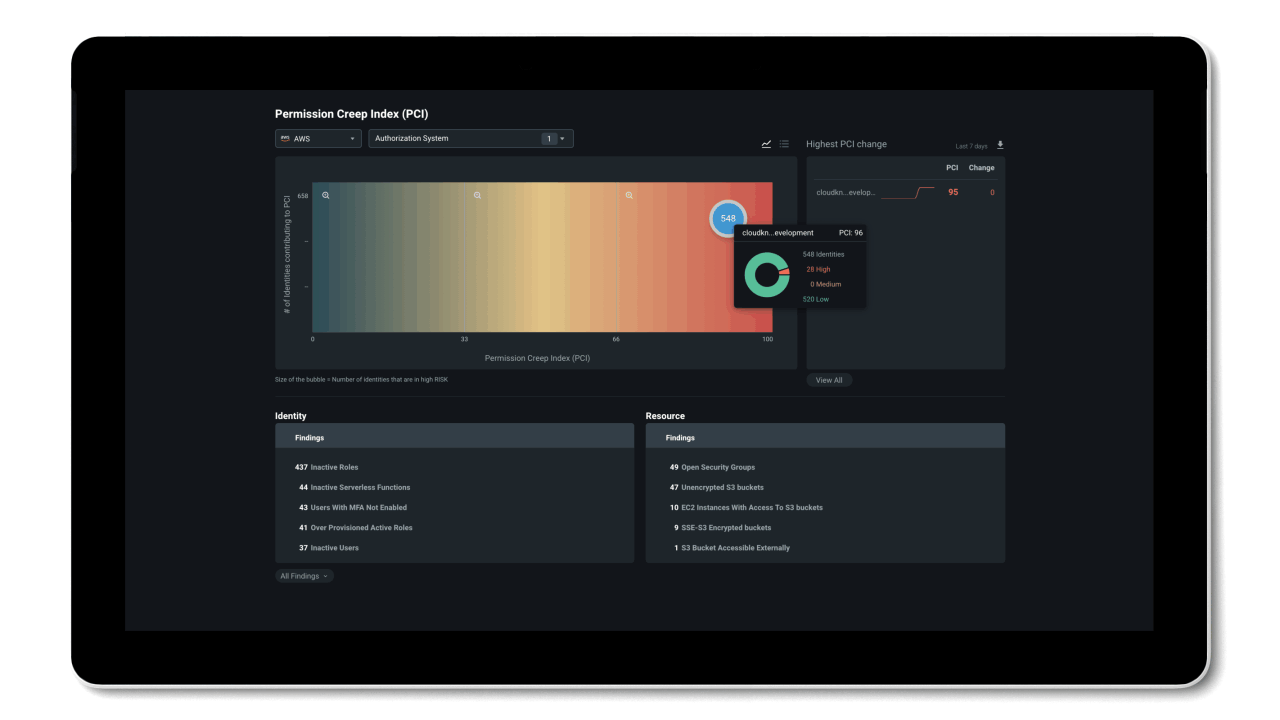
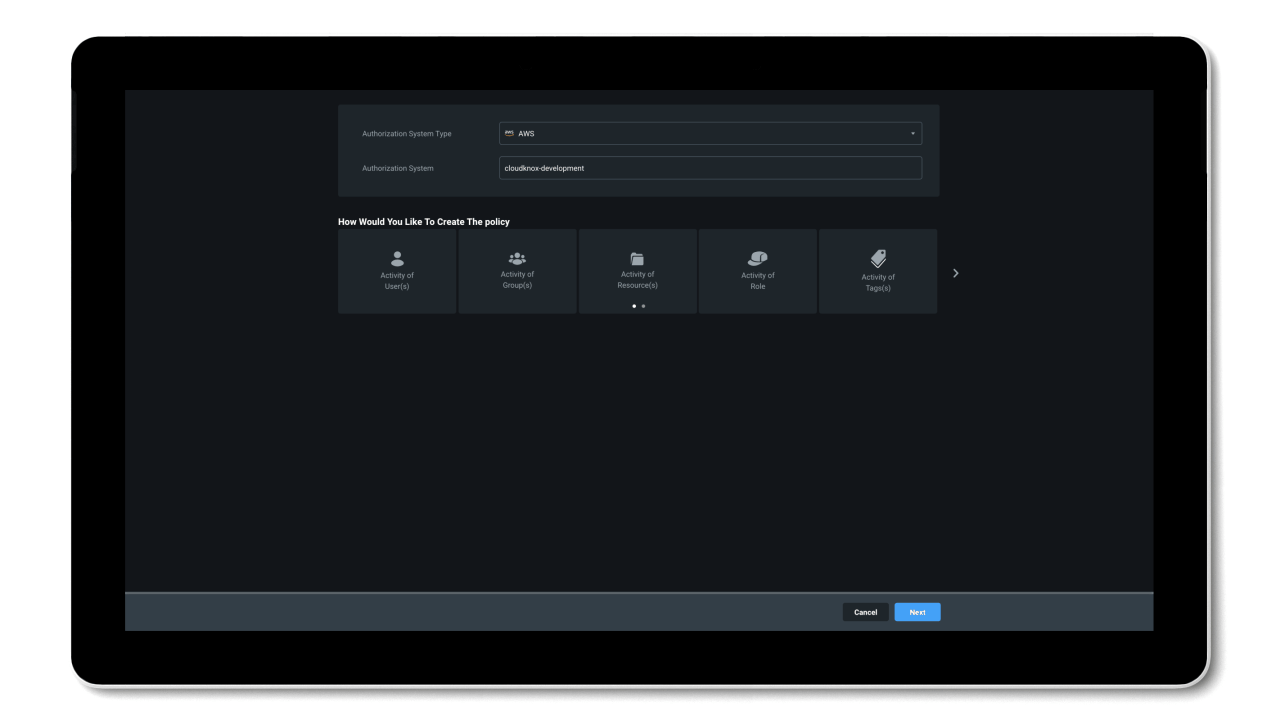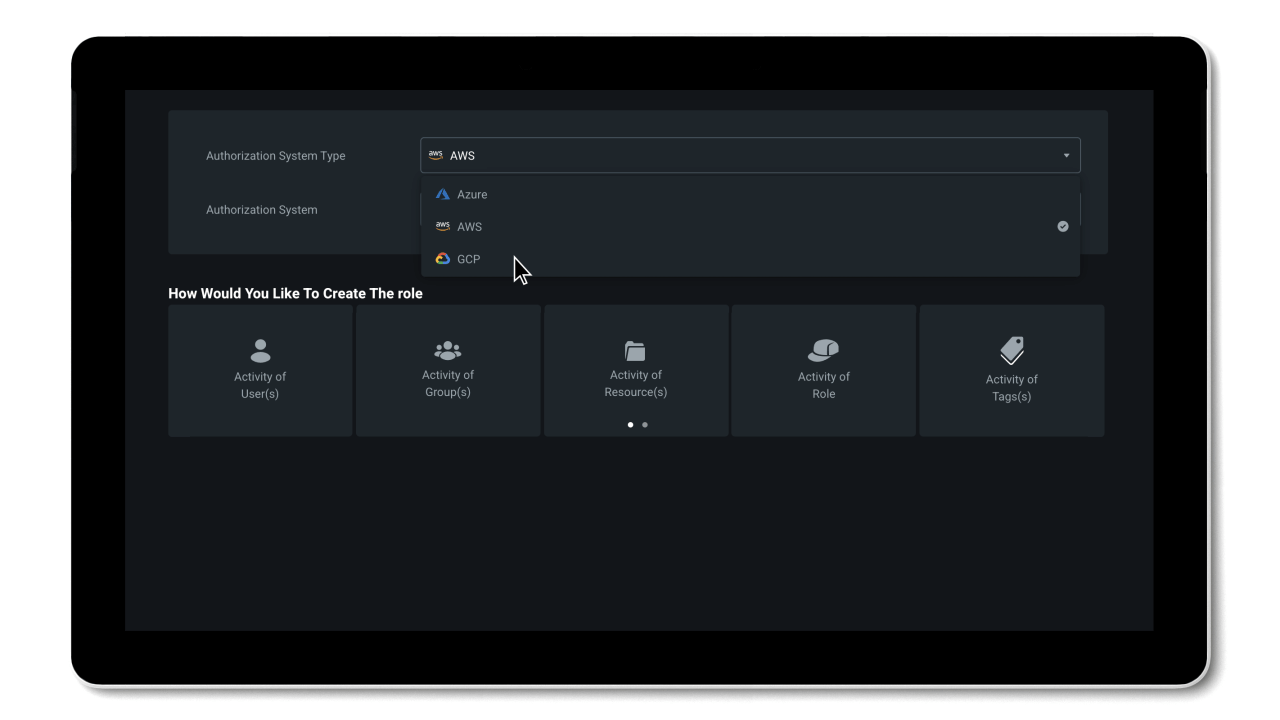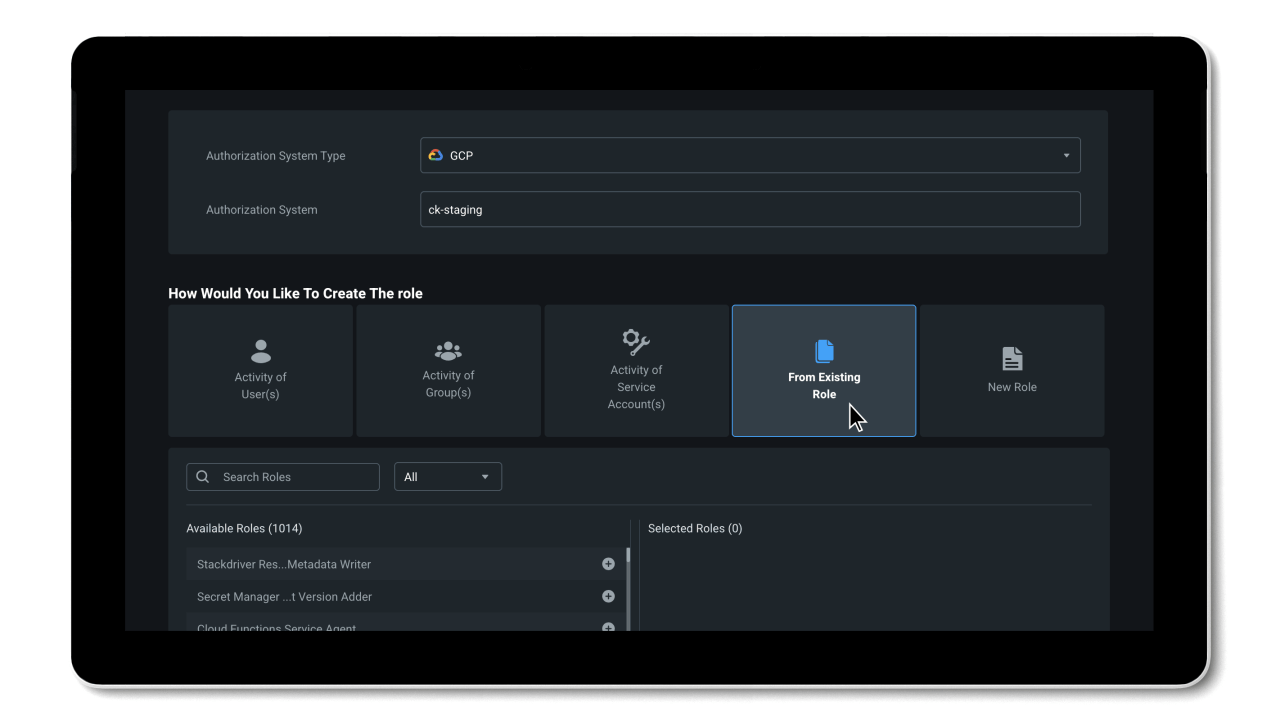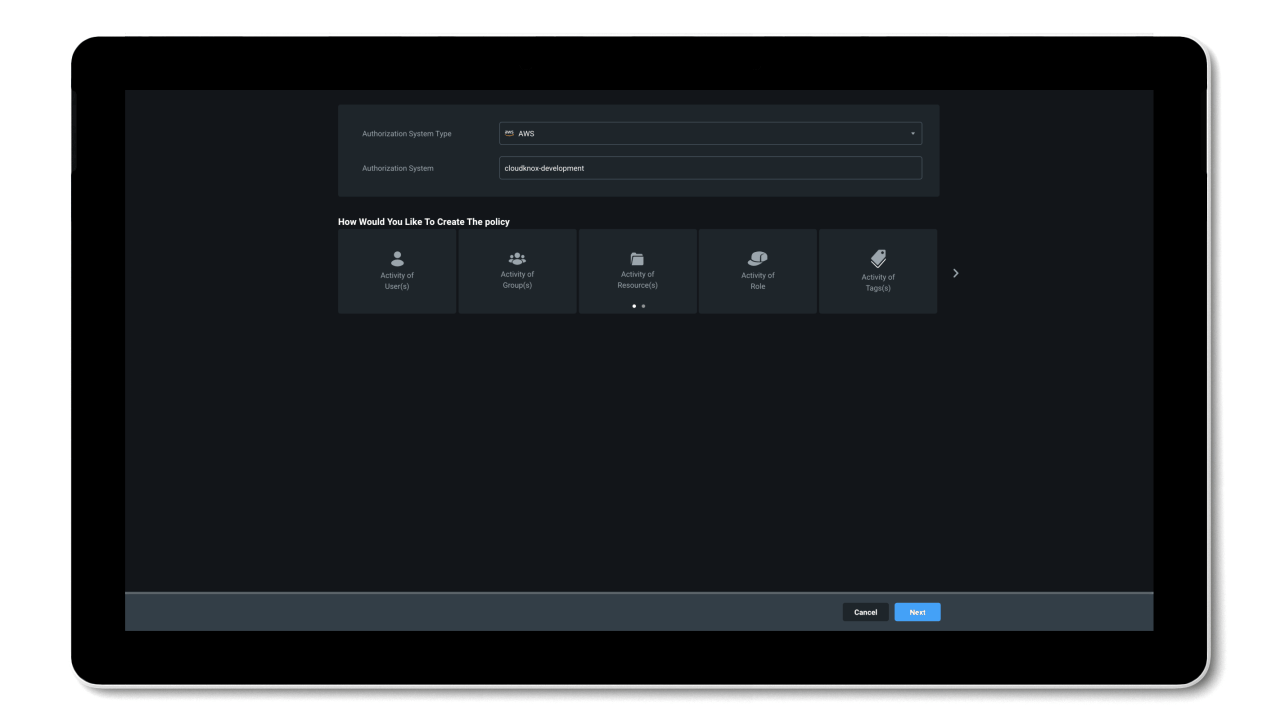
Manage permissions based on historical usage and activities
By working towards a Zero Trust security model, organizations can reduce their permissions gap and secure their environment. The problem is, implementing least privilege access policies is almost impossible to do manually at cloud scale.
To efficiently reduce permission risks, organizations need to shift from static processes that grant permissions based on job roles and assumptions, to a dynamic solution that can right-size permissions based on historical data.
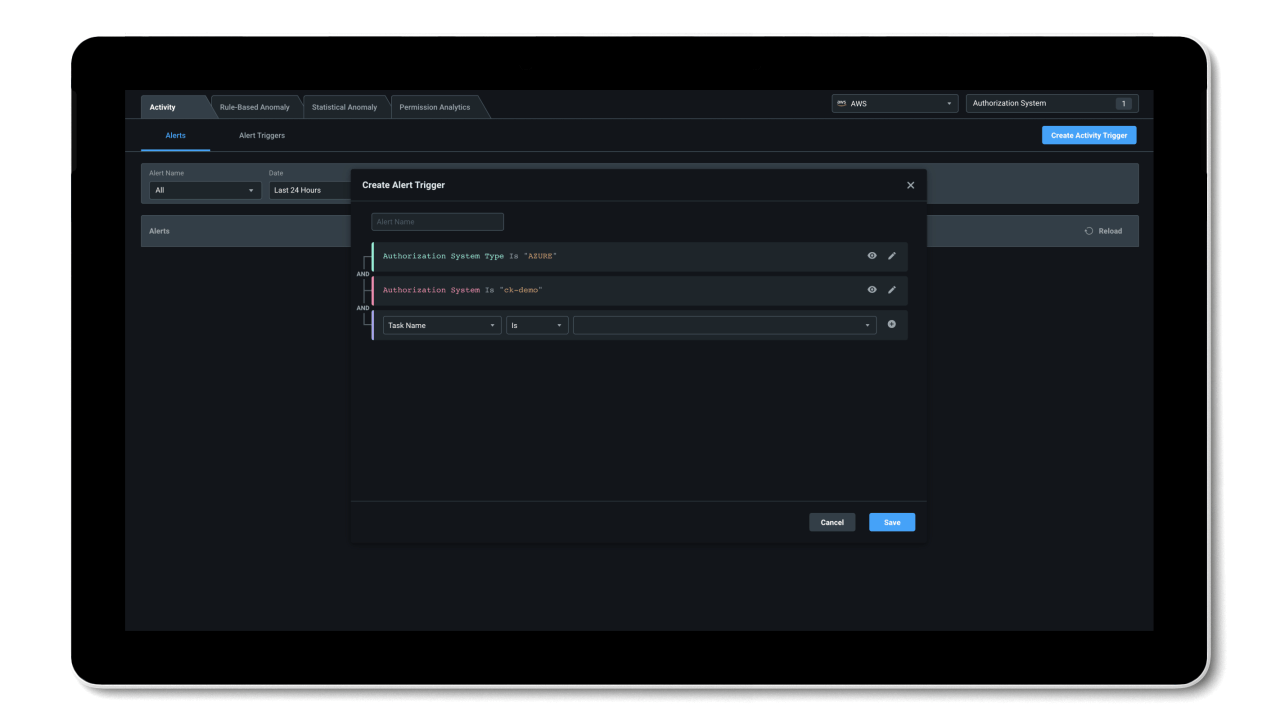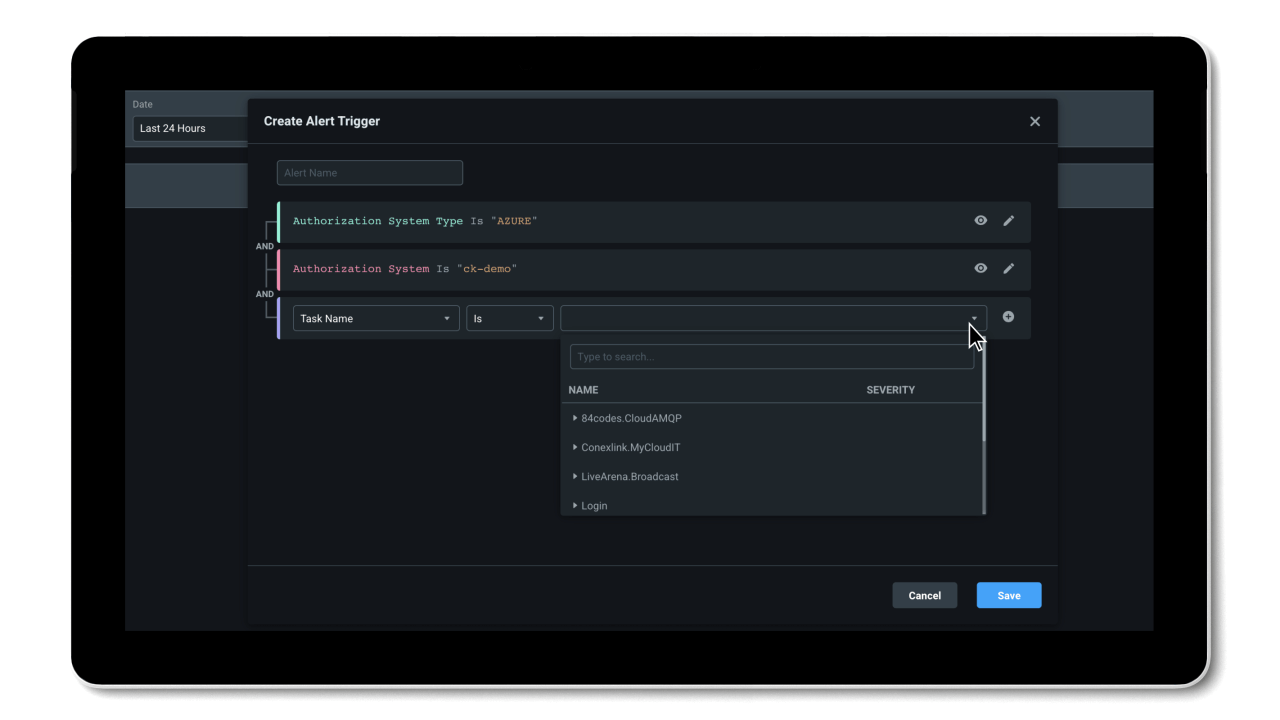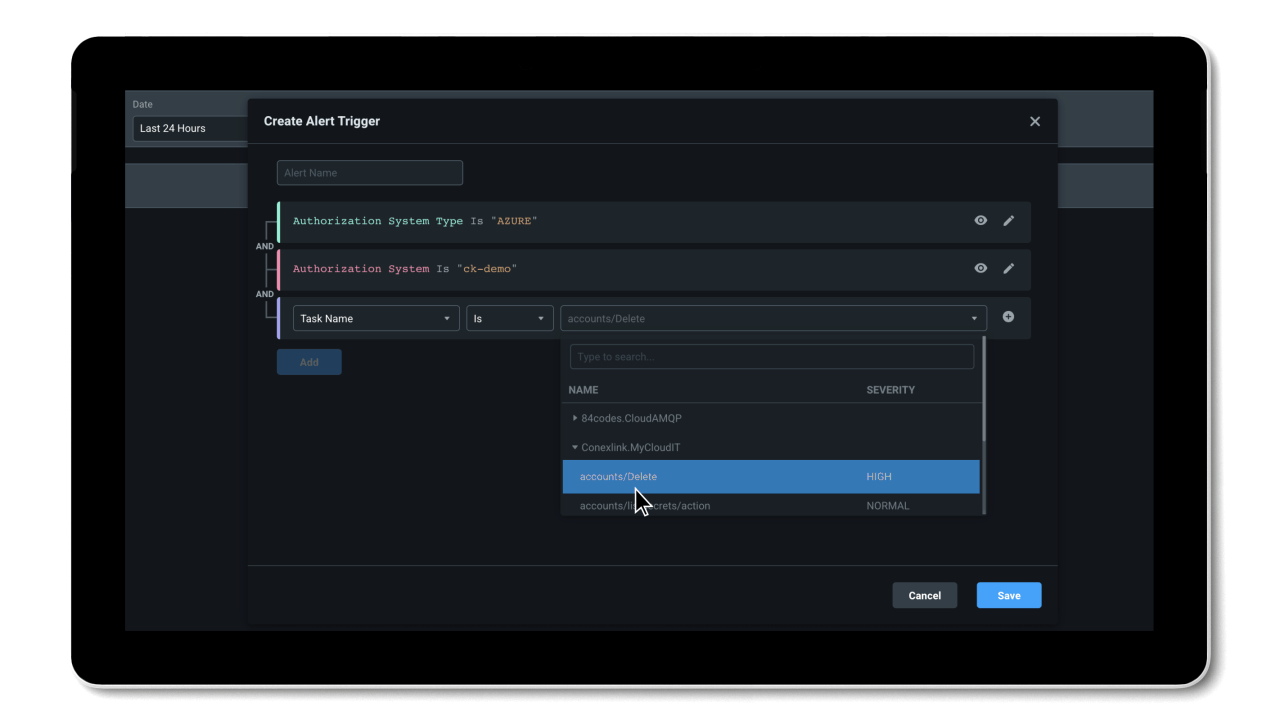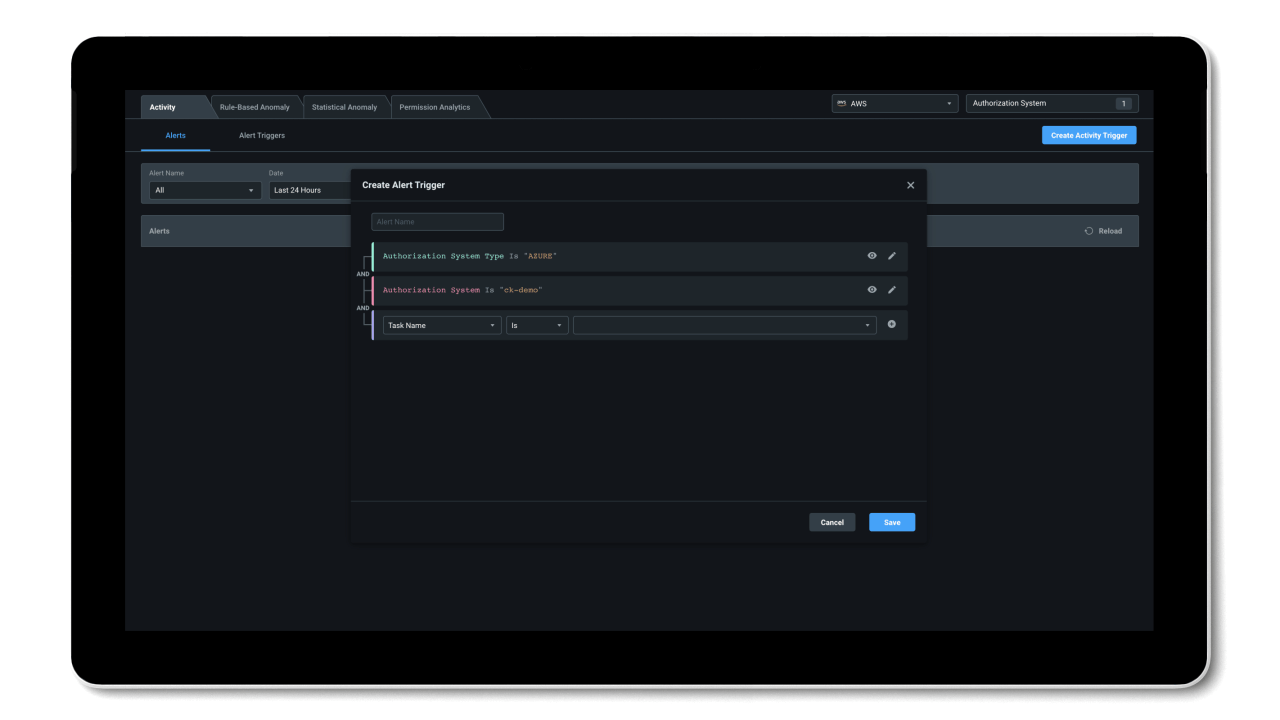
Entra Permissions Management provides a single unified platform to manage permissions of all identities across all major cloud platforms. With granular cross-cloud visibility and a look into your identities’ historical data, you can easily assess your cloud permissions risks and right-size permissions with just a few clicks. And, thanks to the automation of the principle of least privilege and high-precision ML-based anomaly detection capabilities, Entra Permissions Management helps streamline your threat detection, embrace a Zero Trust strategy, and maintain a strong security posture.