Protecting What Matters: A Threat-Based Approach to Security Assessment
Protecting What Matters: A Threat-Based Approach to Security Assessment
In my last blog, I highlighted the shortcomings of the three most common security assessments. Today, we’ll explore a way to overcome these challenges.
At its most basic level, the job of any security practitioner is to make sure “bad things” do not happen to the organization’s information assets.
The total list of “bad things” that could happen can be boiled down to a relatively short set of threat categories that are manageable (i.e. – malware, user error, phishing, etc.). The likelihood of a particular threat type materializing differs per organization due to its size, public profile, industry, etc.
Protecting What Matters
Threats are only meaningful in relation to your organizational assets. By correlating our likely threats to the security controls of our most valuable assets (and assets related/interconnected with them), we can build a reasonable model for estimating our organization’s level of protection against specific and likely threats. This is how we begin to answer the all-important question discussed in my last blog, “how secure are we?”
This model can also serve as a roadmap for the question, “where do we go from here?” Rather than starting with the first box on the checklist or with the path of least resistance, you can begin addressing the problems that are likely to cause the greatest impact to your business’ bottom line first – significantly reducing the chances of a catastrophic event.
Finally, focusing on the threats as they relate to business value can serve as a good tool to evaluate which security investments will provide the most benefit to the organization, making it much easier to communicate the need for an increased (or maintained) security budget to the CFO and other non-technical organizational leaders.
A Threat-Based Approach to Security Assessment
When building your security posture, you’ll want to think about specific systems, categories of systems, and data assets. For each asset, there is a fairly standard set of security controls that can be considered (yes, I am injecting a version of a giant best practices checklist here).
Ask yourself the following questions:
- Question 1: What are the assets YOUR company needs to protect?
- Questions 2: What are the threats to those assets?
Now, let’s take a look at this in practice. Say your organization is likely to face a credential harvesting threat. This threat consists of five stages – phishing email, user error, malicious website, credential compromise, and data exfiltration.
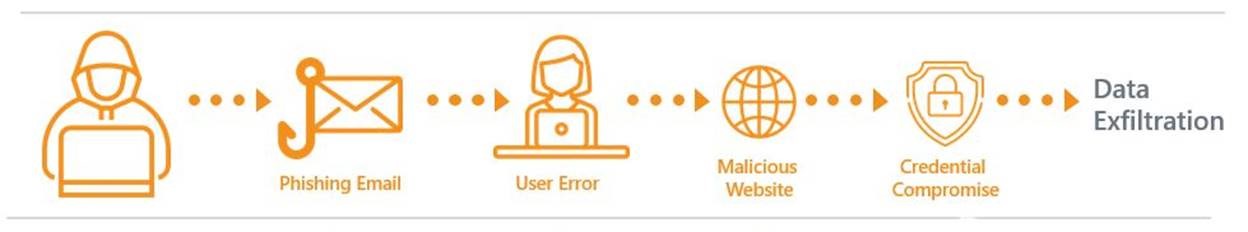
We consider the standard set of security controls that apply at each stage and examine the degree to which they have been implemented.

Based on this assessment, you can provide a relatively good answer for the three primary questions in your security assessment:
- Are we secure? You can now demonstrate the relatively low (in this case) level of protection against a specific threat – and the same process can be exercised for the likely threats you face.
- Where do we go from here? Now that you have a list of likely threats and an assessment of your level of protection – areas of focus should become rather clear.
- Which security investments will provide the most benefit to the organization? Lastly, as you’re pursuing your goal state, you can now model the impact of implementing specific security controls on protection against your set of likely threats.
We feel so strongly that your threat-based assessment should be able to provide meaningful answers – we decided to build a security assessment approach here at BDO Digital. If you are interested in incorporating a measurable security assessment into your organization– contact us to learn more.


SHARE