What Doomsday Preppers Teach Us About Cybersecurity
What Doomsday Preppers Teach Us About Cybersecurity
It’s relatively common for people to prepare for when things go wrong. Many have first aid kits in the closet for the occasional injury. Some may budget for an emergency fund in case they lose their job. But some people take preparedness to the next level by preparing for all sorts of extreme circumstances, like nuclear winters, societal collapse, and even zombie attacks!

Are You Preparing for the Right Threats?
These so-called “Doomsday Preppers” identify a list of potential threats – whether real or perceived – and spend a lot of time and money preparing for how to either prevent or survive them. Some build elaborate panic rooms or underground bunkers. Some invest in elaborate tools, like gas masks, water purifiers, and fire starters. But are they truly protected?
If they use a threat-based security strategy, they might be.
A threat-based strategy first takes one’s assets into account. What are you trying to protect? Your property? Your life? Next, and often more challenging, it determines what are you trying to protect these things from. Invading armies? Hurricanes? Disease? Zombies? Understanding your attackers will help you develop the best fit and most effective strategy to protect what matters most to you.
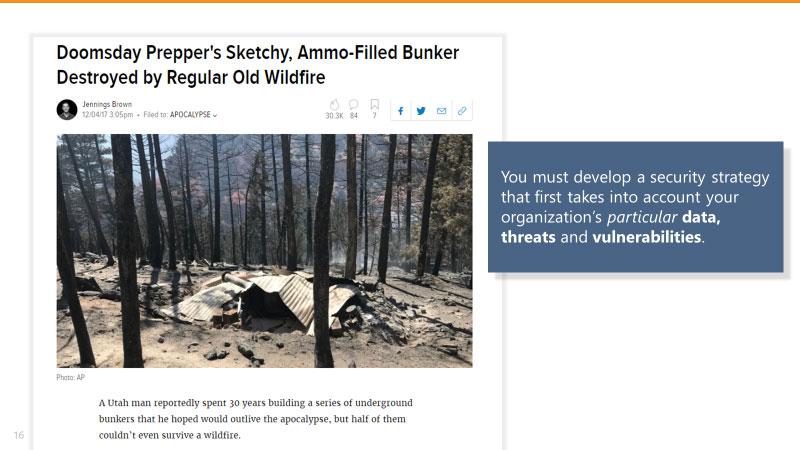
Here’s an example of what not to do.
One prepper spent thousands of dollars and hundreds of hours preparing for disaster. He had built a safe house in the forest, stocked up on food and supplies, and mapped out elaborate escape routes in case of an enemy invasion.

He knew what he wanted to protect. Unfortunately, he didn’t take into consideration part two of the threat-based strategy model – determining the most-likely threat. In this case, a forest fire.
A wildfire spread through the forest and destroyed his home and belongings.
What Businesses Can Learn from Preppers
When trying to prepare for potential cyberattacks, business could learn a thing or two from these examples. Turns out, attempting to prepare for every “bad thing” that could happen isn’t the best way to protect your organization’s data and people.
The total list of “bad things” that could happen can be boiled down to a relatively short set of threat categories that are manageable (user error, malware, phishing). The likelihood of a particular threat materializing differs per organization due to its size, public profile, industry, etc.
So, whether you’re building an underground bunker to keep yourself safe from zombies or developing a cyber defense strategy to protect your organization’s data and people, make sure you enlist a threat-based strategy.
Don’t know where to start?
BDO Digital and Microsoft have developed a threat-based maturity model to help organizations figure out 1) what are they trying to protect within their organization, and 2) what are their most-likely threats? Once you know your “SCORE,” you can then develop the best-fit cybersecurity strategy and choose the best-fit tools for your organization.
Contact us to learn more about BDO Digital's security solutions.


SHARE