Protecting Your Digital Assets: Preventing Token Theft With Microsoft Conditional Access
Protecting Your Digital Assets: Preventing Token Theft With Microsoft Conditional Access
Token theft has emerged as a significant threat to organizations worldwide. Tokens, which are digital keys that allow access to networks and sensitive information, can be a goldmine for cybercriminals if they fall into the wrong hands. However, with the right strategies and tools, businesses can help mitigate the risk of token theft and safeguard their digital assets.
Understanding Token Theft
Token theft occurs when unauthorized individuals gain access to security tokens, which are used to authenticate identity and authorize access to systems and data. These tokens can be stolen through various means, including phishing attacks, malware, or exploiting vulnerabilities in software or networks. Once a token is stolen, attackers can impersonate legitimate users that have successfully passed multifactor authentication (MFA), gaining unauthorized access to confidential information, financial data, and critical systems.
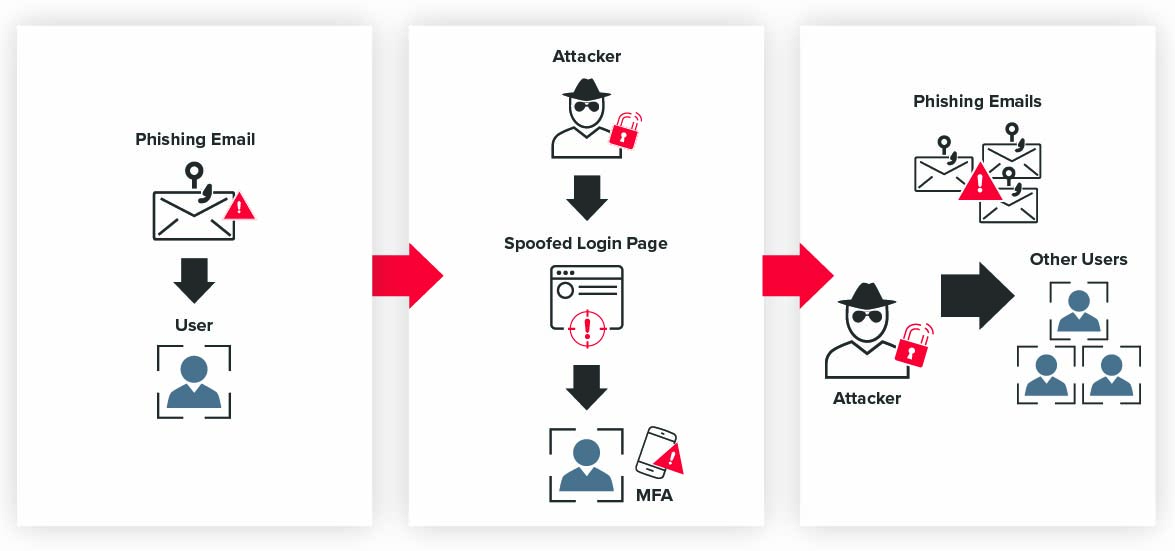
A common situation, pictured below, is a phishing attack. A malicious email is received, and a user clicks on the malicious site. The user enters their password and MFA code into a spoofed website that the attacker controls, meaning the user has completed multifactor authentication on the fake website and has granted the attacker access to their account. In most cases, the attacker will then leverage the user’s account to send more phishing emails to as many other people as possible, knowing the user’s account is more reputable than the original account used for phishing.
The Role of Microsoft Conditional Access
Microsoft Conditional Access is a powerful tool within the Microsoft 365 suite that helps organizations protect their resources from unauthorized access, including the threat of token theft. Combining conditions such as location, device trust and risk-based authentication, Conditional Access can limit or prevent access to a stolen token in the first place.
How it works:

Organization joined machines can be identified with browser plugins to determine what organization they belong to. These plugins report back to Entra ID if the machine is trustworthy. Entra ID can then detect the devices not joined to the organization, and Conditional Access policies can be created to only permit sign-ins from organization joined devices.
Define Risk-Based Conditional Access Policies
Entra ID Identity Protection combined with Microsoft Conditional Access allows organizations to define policies based on the risk level of a sign-in attempt. By integrating with Azure AD Identity Protection, Conditional Access can evaluate the risk of each sign-in attempt in real-time and apply appropriate access controls. For example, users attempting to sign in from an unfamiliar location or device might be required to pass additional authentication challenges.
Use Session Controls
Session controls can limit what a user can do after they've been granted access to a resource. For example, Conditional Access can enforce policies that prevent the download of sensitive documents to unmanaged devices, or limit access to data within a corporate network. This can help mitigate the impact of token theft by limiting what an attacker can do, even if they manage to gain access. Session control can also limit the amount of time a token is valid for - decreasing the amount of time an attacker can leverage the stolen token.
Organizations should address security incidents as soon as they appear, so consistent monitoring is essential. Token theft and other security concerns related to user sign in can be detected by Entra ID Identity Protection. If the alerts are not addressed programmatically by Conditional Access, the attacker could pivot knowing the credentials are valid to try and gain access to a VPN or other areas of an organization. Ensure there is someone watching the alerts around the clock to stop the threat as quickly as possible.
If your IT department doesn't have the bandwidth for 24/7 monitoring, consider engaging with a Managed Security Services Provider (MSSP) to offload some responsibility and allow your team to focus on more value-added initiatives and activities. BDO Digital Active Protect is a comprehensive MXDR solution that leverages the Microsoft suite of security tools coupled with our managed security operations center (SOC) to provide continuous protection, detection, and response.
Conclusion
Token theft poses a significant threat to organizations, but with the right strategies and tools, such as Microsoft Conditional Access, Entra ID Identity Protection, and 24/7 monitoring, it is possible to mitigate the risks. As the cybersecurity landscape continues to evolve, staying ahead of threats like token theft will be crucial for maintaining the integrity and confidentiality of sensitive information. It's important for organizations to ensure they are working with the most current information and practices to best protect their digital assets.
View Microsoft's playbook to see how they recommend addressing token theft.
Related Resources
The Hidden Risks of Legacy Technology in Financial Services
April 18, 2024The Hidden Risks of Legacy Technology in Financial Services
April 18, 2024In the rapidly evolving landscape of financial services, banks find themselves at a crossroads between innovation and operational security.
How to Upgrade Data Security Before Adding AI: Five Steps
April 15, 2024How to Upgrade Data Security Before Adding AI: Five Steps
April 15, 2024While these new artificial intelligence tools are helpful for generating approaches and content based on natural language queries, they also pose potential risks of exposing sensitive data or violating compliance regulations.
Elevating Cybersecurity for Energy Industries: The Necessity of Modernizing Legacy Systems
April 10, 2024Elevating Cybersecurity for Energy Industries: The Necessity of Modernizing Legacy Systems
April 10, 2024As the energy and utilities industry increasingly incorporate Internet of Things (IoT) technologies into their operations, the cybersecurity stakes are rising in parallel.
Everything To Know About Microsoft Security Copilot
April 3, 2024Everything To Know About Microsoft Security Copilot
April 3, 2024Microsoft made their Copilot for Security tool generally available on April 1, 2024. With its advancements in speed and scalability, this generative AI-powered cybersecurity assistant is poised to revolutionize cybersecurity.

SHARE