Top 4 Cybersecurity Mistakes Midsize Organizations Make - And How to Avoid Them
Top 4 Cybersecurity Mistakes Midsize Organizations Make - And How to Avoid Them
73% of cybersecurity breaches are financially motivated, according to the 2017 Verizon Data Breach Investigations Report. This means the attackers are after your organization’s data to sell on the black market. It's not always the big enterprises and the huge payday that they're after. Cybercriminals are targeting mid-market organizations because they know they might not have the big budgets to establish top-notch security, and therefore small and midsize organizations are an easier target.
Attackers are opportunistic. They start by using low-tech methods of scanning and phishing to find initial entry points or vulnerabilities, then probe further using manual methods.
In our work with clients, we've run countless security assessments to uncover the vulnerabilities of mid-market organizations. Our experience tells us that these 4 cybersecurity mistakes are the most common.
Skipping Phishing Assessments
The vast majority of attackers enter networks through the same vulnerable channel using the same proven method – exploiting your users via a phishing email. Organizations need to keep their users sharp by providing security awareness training along with sending test phishing emails. This prepares users to respond correctly when faced with a real phishing email. The clicks are tracked and used to follow up with groups or individual users outside of company-wide training.
The average click rate during phishing assessments is around 10%, with the manufacturing industry having the top average click rate of 13%, according to Verizon. This presents a major risk since all it takes it one click for an attacker to enter your network. If the workstations have vulnerable software or a weak configuration, this makes things worse.
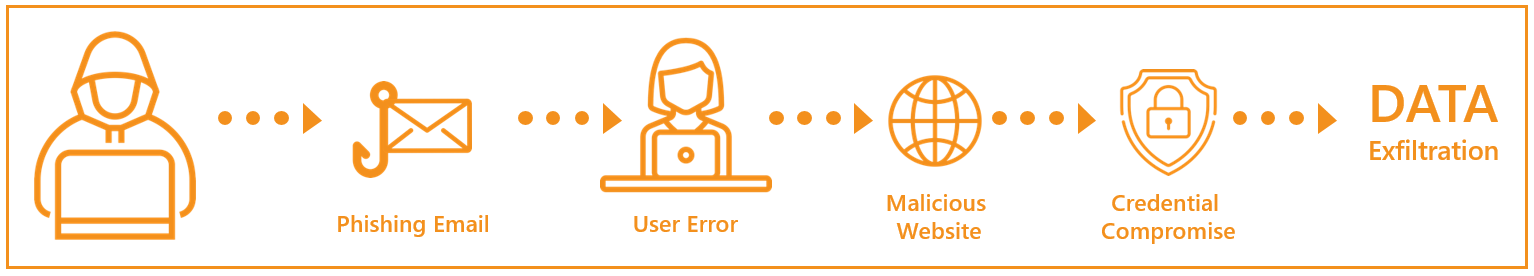
Humans are the weakest link. Performing social engineering training and phishing tests is one of the most important areas of a cybersecurity program. 90% of security breaches involve phishing or social engineering. If your organization’s click-rate during a phishing assessment is not in the single digits, you are higher than the industry average and at a higher risk than your peers. Because of these trends, BDO Digital's year-round phishing assessment program has become a popular security managed service.
Ignoring Security Monitoring
Most mid-market organizations don’t have the budget or staff to respond to security incidents 24x7 or perform routine security reporting. It is also common to not pay attention to activity alerts and logs from systems like Active Directory, firewalls, file servers, email or SharePoint.
Having a solid monitoring and reporting routine will help avoid, catch, and privilege misuse or insider activity. One of the first milestones of a successful cybersecurity attack cycle is to gain domain admin privileges. One of the easiest ways to accomplish this and remain untracked is to create a new domain admin account disguised as a generic service account. This activity will go unnoticed without specific alerts being configured.
Monitoring and reporting on security events from next-gen firewalls allow IT teams to fine-tune the solution, ensure it is operating effectively, block attacks in real time and highlight any malware in the environment attempting to “phone home”. We found during our security assessments that most customers perceive the idea of setting up this sort of monitoring and reporting system and routine as overwhelming. This is why many customers are turning to BDO Digital's managed firewall service as part of our suite of security managed services.
Not Protecting the Identity of Your users
In today’s world, protecting the corporate network does not stop at the firewall. Users are mobile and need to connect from untrusted networks to get their job done and maximize productivity. It is common for employees to have hardened company-issued laptops, however many organizations allow employees to connect to corporate email and other data with their personal mobile phones.
Without a Mobile Device Management (MDM) solution, companies have no assurance their data and user accounts are protected. Multifactor authentication is also now a common requirement for any remote access such as VPN or email. Using Conditional Access as part of Microsoft’s Enterprise Mobility + Security (EMS) requires a baseline level of trust to access data in Azure and Office 365.
With the addition of cloud services and SaaS platforms, employees might need to manage multiple individual usernames and passwords. This can be difficult to secure and difficult for users to remember all passwords. The more passwords there are to remember, the more susceptible they are to writing passwords down, which is human nature. To mitigate this risk, SaaS solutions need to be configured with Single-Sign-On (SSO) to use one single source of truth such as an Azure Active Directory. As part of Azure Active Directory Premium, companies can enable SSO for more than 3000 common applications with a few clicks. This feature is included in Microsoft’s Enterprise Mobility + Suite (EMS) E3.
Unmeasured Security Posture
Setting up a framework for measuring your security program will allow your organization to measure its maturity and risk. It also allows them to measure if you are improving or declining over time as industry conditions change. This a key component of any risk management program.
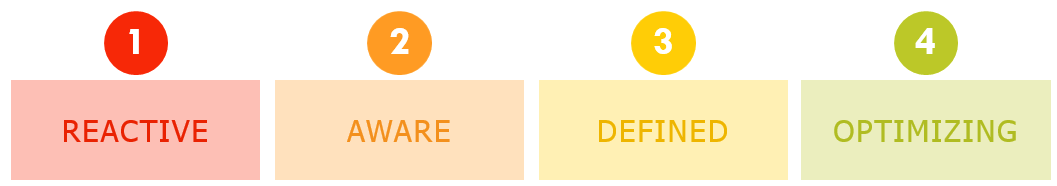
The first step is to decide what controls and KPIs (Key Performance Indicators) make sense to measure for the organization. This starts with governance and a top-down approach. If a company has compliance requirements, the framework typically matches the compliance requirements at a minimum. A gap analysis and risk assessment can be done against these this framework. Then, implementing policies, procedures, controls, and monitoring will bring a company into a state of a cybersecurity program that is continuing to optimize.


SHARE